Here i discussed about, How do you can plan for alternate access mappings in your MOSS 2007 environment.
In this article, I will discuss on :
About alternate access mappings
Reverse proxy publishing
Alternate access mapping integration with authentication providers
Alternate access mapping integration with Web application policies
Alternate access mapping and external resource mapping
Troubleshooting alternate access mappings
Alternate access mappings direct users to the correct URLs during their interaction with Microsoft Office SharePoint Server 2007 (while browsing to the home page of a Office SharePoint Server 2007 Web site, for example). Alternate access mappings enable Office SharePoint Server 2007 to map Web requests to the correct Web applications and sites, and they enable Office SharePoint Server 2007 to serve the correct content back to the user.
Alternate access mappings have been implemented because there are common Internet deployment scenarios in which the URL of a Web request received by Internet Information Services (IIS) is not the same as the URL that was typed by an end user. This is most likely to occur in deployment scenarios that include reverse proxy publishing and load balancing.
About alternate access mappings
Alternate access mappings enable a Web application that receives a request for an internal URL, in one of the five authentication zones, to return pages that contain links to the public URL for the zone. You can associate a Web application with a collection of mappings between internal and public URLs. Internal refers to the URL of a Web request as it is received by Office SharePoint Server 2007. Public refers to the URL of an externally accessible Web site. The public URL is the base URL that Office SharePoint Server 2007 uses in the pages that it returns. If the internal URL has been modified by a reverse proxy device, it can differ from the public URL.
Multiple internal URLs can be associated with a single public URL. Mapping collections can contain up to five authentication zones, but each zone can only have a single public URL. Mapping collections correspond to the following authentication zones:
Default
Intranet
Internet
Custom
Extranet
Reverse proxy publishing
A reverse proxy is a device that sits between end users and your Web server. All requests to your Web server are first received by the reverse proxy device and, if those requests pass the proxy's security filtering, the proxy forwards the requests to your Web server. Reverse proxies can perform advanced functionality, such as receiving a Web request over the Internet by using HTTPS (Hypertext Transfer Protocol over Secure Socket Layer), but forward the request to the server by using HTTP. This is referred to as "off-box SSL termination." Reverse proxies can forward the request to a port number other than the port on which the request was originally received. Reverse proxies can also change the HTTP Host header field.
Office SharePoint Server 2007 is compatible with many reverse proxy servers, but in the following example the publishing rule is from the reverse proxy software, Microsoft Internet Security and Acceleration (ISA) Server 2006. ISA Server 2006 includes a publishing wizard to help you create a publishing rule for Office SharePoint Server 2007. After the rule is created, you can modify it at any time.
Configuring the reverse proxy server
The first two figures in this example show a modified publishing rule where the Forward the original Host header option is turned off to help demonstrate the flexibility of alternate access mapping. If the Forward the original Host header option is selected, the public hostname also serves as the internal hostname when configuring alternate access mapping.
The following figures show the Listener tab and Public Name tab on the properties sheet for the rule. These properties define the URL to use to access your Web application. This URL is actually the URL of your reverse proxy server, which forwards the request to your server running Office SharePoint Server 2007.
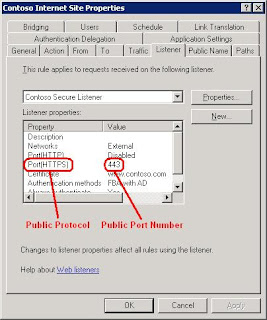
The end user's URL is made up of the public protocol, the public hostname, and the public port number, as shown in the following table.
Public protocol Public Hostname Public port number Public URL
HTTPS + "://" + www.contoso.com + ":" + 443 = https://www.contoso.com
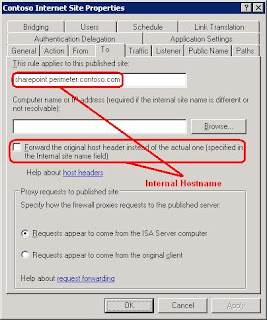
The following figures show the To tab and Bridging tab on the properties page for the rule. These properties define the URL that the reverse proxy server uses to forward the request to your server running Office SharePoint Server 2007.
Configuring the SharePoint Web application
After you have configured the reverse proxy server publishing rule, configure your Web application and alternate access mappings to match the publishing rule. You can do this by extending an existing Web application to an additional IIS Web site specifically for the reverse proxy publishing rule. You can also create a new Web application for this publishing rule. The values you need to enter are the same in either case.
Use the following procedure to extend an existing Web application.
Extend an existing Web application
1) From Administrative Tools, open the SharePoint Central Administration Web site.
2) On the Central Administration home page, click Application Management.
3) On the Application Management page, in the SharePoint Web Application Management section, click Create or extend Web application.
4) On the Create or Extend Web Application page, click Extend an existing Web application.
5) On the Extend Web Application to Another IIS Web Site page, select a Web application. When you have selected a Web application, enter values for the port, Host header, and SSL fields, based on the internal URL properties defined in "Configuring the reverse proxy server" earlier in this article. In the URL field, enter the public URL defined in "Configuring the reverse proxy server," as shown in the following figure.
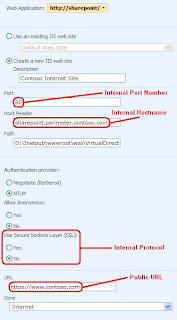
6) Select an alternate access mapping zone to assign this extension of your Web application to. There are a maximum of five zones available for each Web application. In this example, we will use the Internet zone. All of the zones provide the same functionality, although the Default zone will always be used for certain features, such as sending administrative e-mail messages to site collection owners.
7) To create the IIS Web site, click OK.
After you have completed these procedures, verify that your public URL was created correctly in alternate access mappings and then add your internal URL. Unless your internal URL is the same as your public URL, this is an extra step that you must perform manually.
Use the following procedure to view the Alternate Access Mappings page.
View the Alternate Access Mappings page
1) From Administrative Tools, open Central Administration.
2) On the Central Administration home page, click Operations.
3) On the Operations page, in the Global Configuration section, click Alternate access mappings.
4) On the Alternate Access Mappings page, select the Web application to publish through the reverse proxy server.
At this point, you should see alternate access mapping URLs assigned to your Web application, as shown in the following figure.
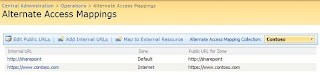
The public URL from the reverse proxy publishing rule has been assigned to the Internet zone of your Web application. Use the following procedure to add the internal URL from the reverse proxy publishing rule to the Internet zone of your Web application.
Add the internal URL from the reverse proxy publishing rule to the Internet zone of your Web application
1) On the Alternate Access Mappings page, click Add Internal URLs.
2) Type the name of the internal URL and select the same zone that you used for the public URL. In this example, we will use the Internet zone.
3) Click Save.
At this point, you should see that the additional URL is assigned to your Web application (in the same zone as the public URL of your reverse proxy publishing rule), as shown in the following figure.
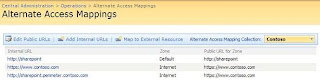
When a user browses to https://www.contoso.com, the Web request will be received by the reverse proxy server and forwarded to http://sharepoint.perimeter.contoso.com. Office SharePoint Server 2007 will then receive the Web request, see that the URL of the request is http://sharepoint.perimeter.contoso.com, find that this URL is assigned to the Contoso Web application, and return the content from that Web application. In addition, because the http://sharepoint.perimeter.contoso.com URL is assigned to the Internet zone, Office SharePoint Server 2007 will generate links on the pages by using the public URL for that zone: https://www.contoso.com. This ensures that end users are taken to the proper URL when clicking links on the page.
Load balancers work similarly, especially if they overwrite the end user's original URL with the URL of the individual Web server that the request is being load balanced to. To account for these overwritten URLs, just add the alternate access mappings for the URLs of each individual Web server, as internal URLs, and associate them to the same zone as the public URL of the end user. If they preserve the original URL, then simply have the original URL be the public URL.
Alternate access mapping integration with authentication providers
Alternate access mappings allow you to expose a Web application in as many as five different zones, with a different IIS Web site backing each zone.
Not only do these zones allow you to use multiple URLs to access the same Web application, they also allow you to use multiple authentication providers to access the same Web application.
When extending a Web application into a zone, you have to use Windows authentication provided by IIS. After the Web application has been extended into the zone, you can modify the zone to use a different type of authentication.
Use the following procedure to modify the authentication configuration for a zone.
Modify the authentication configuration for a zone
1)From Administrative Tools, open Central Administration.
2) On the Central Administration home page, click Application Management.
3) On the Application Management page, in the Application Security section, click Authentication providers.
4) On the Authentication Providers page, select your Web application, listed in the Web Application box.
5) Click the name of the zone whose authentication configuration you want to modify.
6) On the Edit Authentication page, in the Authentication Type section, select the authentication type you want to use for this zone:
Windows
Forms
Web single sign on
7) Modify any other authentication configuration settings that you want to change and click Save.
At this point, you can change authentication configuration settings for any other zone as well. You can configure completely independent authentication settings for different zones accessing the same content. For example, you might configure some content to be anonymously accessible while other content requires credentials. You could configure one zone to have anonymous access enabled and all other forms of authentication disabled, guaranteeing that only the anonymous content will be accessible. At the same time, another zone can have anonymous access disabled while NTLM authentication is enabled, guaranteeing that only authenticated access will be allowed. In addition, you can have different types of accounts to access the same content: one zone can be configured to use Windows Active Directory accounts while another zone can be configured to use non–Active Directory accounts with ASP.NET forms-based authentication.
Alternate access mapping integration with Web application policies
Web application policies allow administrators to grant or deny access to accounts and security groups for all sites exposed through a zone. This can be useful for a variety of scenarios.
For example, the Office SharePoint Server 2007 search crawler must go through the same authorization infrastructure as everyone else: it can only crawl content that it has access to. However, users would still like search to crawl restricted content so that authorized users can find that content in search results. The search service uses a Full Read policy on the Web applications to give its crawler permission to read all content on that Web application. That way, it can crawl and index all existing and future content, even content that the site administrator has not explicitly given it access to.
Another example would be Helpdesk personnel who need administrative access to Office SharePoint Server 2007 sites so that they can assist users. To do this, you can create a Web application policy that grants the Helpdesk staff accounts Full Control permission so that they have full administrative access to all current and future sites on the Web application.
Because policies are tied to both Web applications and their zones, you can ensure that the policy you have applied to one zone does not affect other zones. This can be useful if you have content exposed both on the corporate network and to the Internet. For example, suppose you have given a Helpdesk staff account Full Control permission over a Web application's zone that has been assigned to the corporate network. If someone were to try to use that account to access the site over the Internet, that Full Control policy would not apply because it would recognize that the URL is in a different zone. Therefore, the account would not automatically be given administrative access to the site.
Alternate access mapping and external resource mapping
Office SharePoint Server 2007 allows you to extend the alternate access mapping functionality to content that is not hosted within the Office SharePoint Server 2007 farm. To configure this functionality, browse to the Alternate Access Mappings page and click Map to External Resource. You will then be asked to create an entry for an external resource, which you can think of as another Web application. After you have an external resource, you can assign different URLs and zones to it in the same way that you do for Web applications. This feature is not utilized in Office SharePoint Server 2007, but third-party products that build on top of Office SharePoint Server 2007 can make use of it.
For example, the search technology in Office SharePoint Server 2007 is able to crawl content external to the farm such as file shares and Web sites. If that content is available at different URLs on different networks, you would want search to return results by using the appropriate URLs for the user's current network. By using alternate access mapping's external resource mapping technology, search can remap the external URLs in its search results to match the user's zone.
---------- Have A Nice Time ------------------


No comments:
Post a Comment